|
OBJECTIVE |
To understand and use the Risk Matrix as a tool in assessing risks and threats |
|
TIMING |
75 minutes |
|
TIME BREAKDOWN |
Introduction - 10 minutes Group Exercise - 40 minutes Work in pairs - 15 minutes Feedback & Closing remarks - 20 minutes |
|
MATERIALS NEEDED |
Flip charts & marker pens |
|
PREPARATION |
Draw the Risk Matrix on the flip chart, or use a slide |
When planning and facilitating this session, it is important to consistently apply an intersectional lens to each participant's identity and experiences, and their protection needs. Overlapping systems of discrimination and privilege, such as gender, sexual orientation, religion, disability, racial and/or ethnic origin, economic status/class, marital status, citizenship, age and physical appearance, can have a profound impact on human rights defenders' and their communities' perception of and experience with risks and protection.
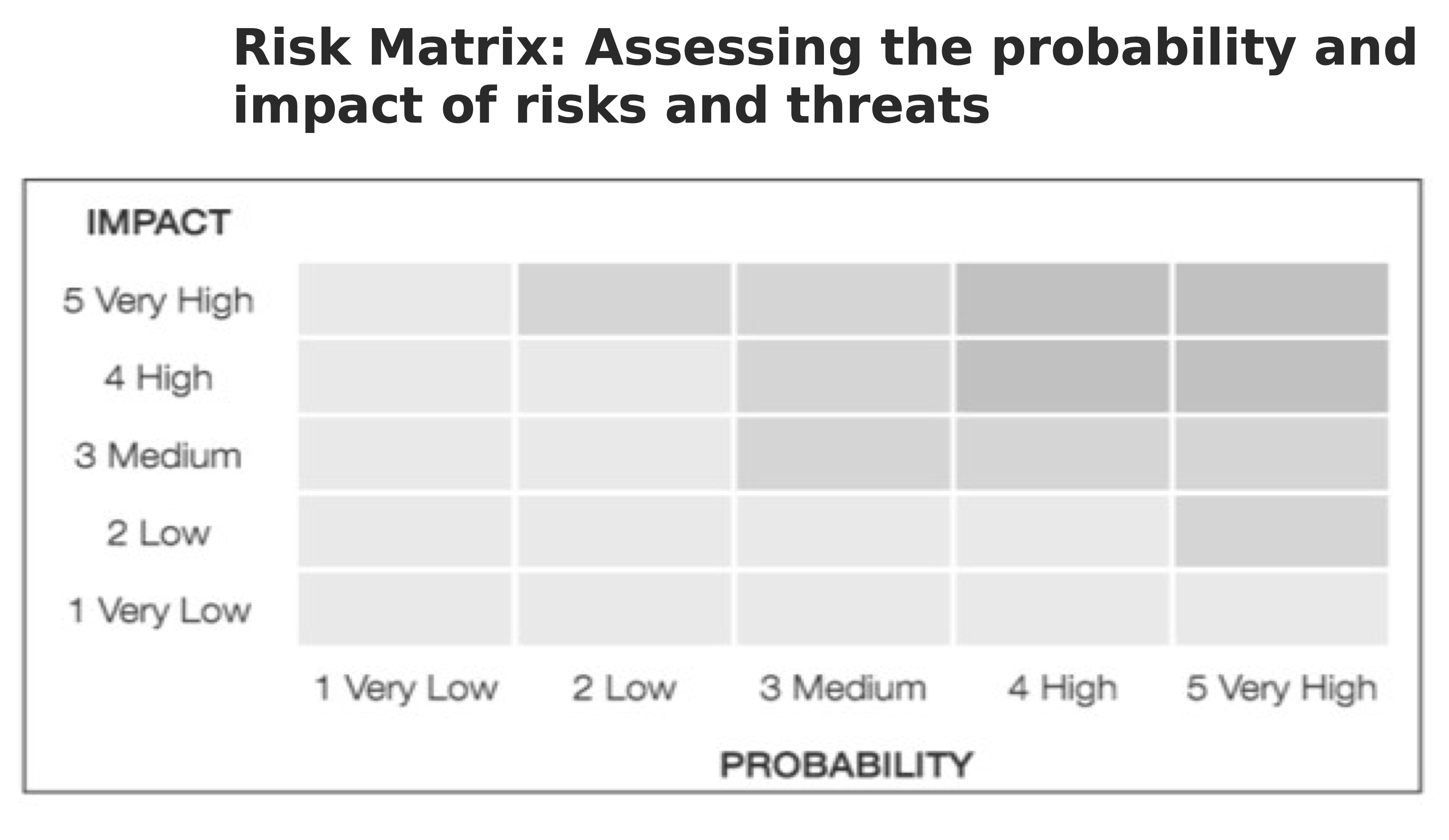
Risk Matrix: Assessing the probability and impact of risks
Probability (or likelihood) of threats and their impacts can be plotted on a graph called the Risk Matrix. The Risk Matrix will help you identify which are the most serious threats – those with higher probability and higher impact.
Probability is along the bottom, ranging from very low probability to very high. Impact is plotted vertically.
For each threat you have, you need to consider how probable it is and what the impact will be.
The Risk Matrix:
Note for facilitator: if this is the first time you are using a risk analysis tool, with the group use a simple example first. For example: “Your friend has just passed their driving test and has bought a second hand car. They are arriving from the countryside and will be driving in [name of city known to all the participants for challenging traffic conditions]. Then go through the steps below.
Group Exercise:
Take 2 examples of threats previously identified by participants, ideally one which is high probability and high impact (eg physical attack), and the other which is lower (eg online insults).
Ask the participants:
What is the level of probability and what might be the likely impact if YOU face this?
When determining probability, consider the following:
- Recent history of threats and direct actions carried out by the aggressor
- Resources of the aggressor
- Amount of damage your work does to the aggressor
- Ability of the authorities to protect you (in cases where they are not the aggressors themselves)
- Your organisation's level of political influence which can neutralise the risk
When assessing the impact, consider the likely effects:
- On individuals, their family, their colleagues
- On property and resources
- On reputation and image
- On the continuity of the work
Emphasise that assessing the probability and impact of risks is a subjective exercise, and can be different for everyone. Your identity, context, resources, role, responsibilities, knowledge, skills, personal capacities, situation and willingness to accept risk are factors which will be unique.
Ask “What can be done to reduce the probability?”
After a number of contributions, ask if the group agrees a lower risk level is now appropriate
Then ask “What can be done to reduce the impact?” and take suggestions intended to lower the impact
Point out the shaded boxes on the Risk Matrix. The darkest shade suggests the risk is so high that the risky activities should stop, or the defenders should consider temporary relocation. The middle shade shows that strong plans are needed. The lightest shade requires less attention when first creating plans, and can be dealt with later.
Work in pairs:
Ask the participants to work in pairs, each to contribute one of the threats they identify and decide where it belongs on the risk matrix, and what can be done to reduce the probability and impact.
Discussion and conclusion:
The facilitator invites participants to share any challenges.
Finally the facilitator concludes:
- The next sessions will develop the protection plans
- First we must always try to reduce probability by Standard Operating Procedures (SOPs)
- Even if we reduce probability, an attack can still take place, so we need to plan in advance how to reduce the impact – this is a Contingency plan
